Internal Date is an IMAP Message Attribute that indicates the internal date and time of a message on an IMAP server. This is a different timestamp than the Origination Date field found in the message header and can be instrumental in authenticating email messages on an IMAP server.
Let’s start with an example. The perpetrator wants to fabricate an email message and make it look like he sent it back in December 2016 from his GoDaddy email account to the Yahoo! email account of his business partner.
He takes a genuine message between the parties from December 2017, edits the subject and the message body to his heart’s content and makes sure to pick a suitable date in December 2016.
He considers producing this forged email message directly. But then, wouldn’t it be more realistic if this message were on the email server? So, he opens Thunderbird where he has his GoDaddy account set up and drags the forged email into his “Sent Items” folder. Thunderbird thinks for a second or two, and voilà—the message is there!
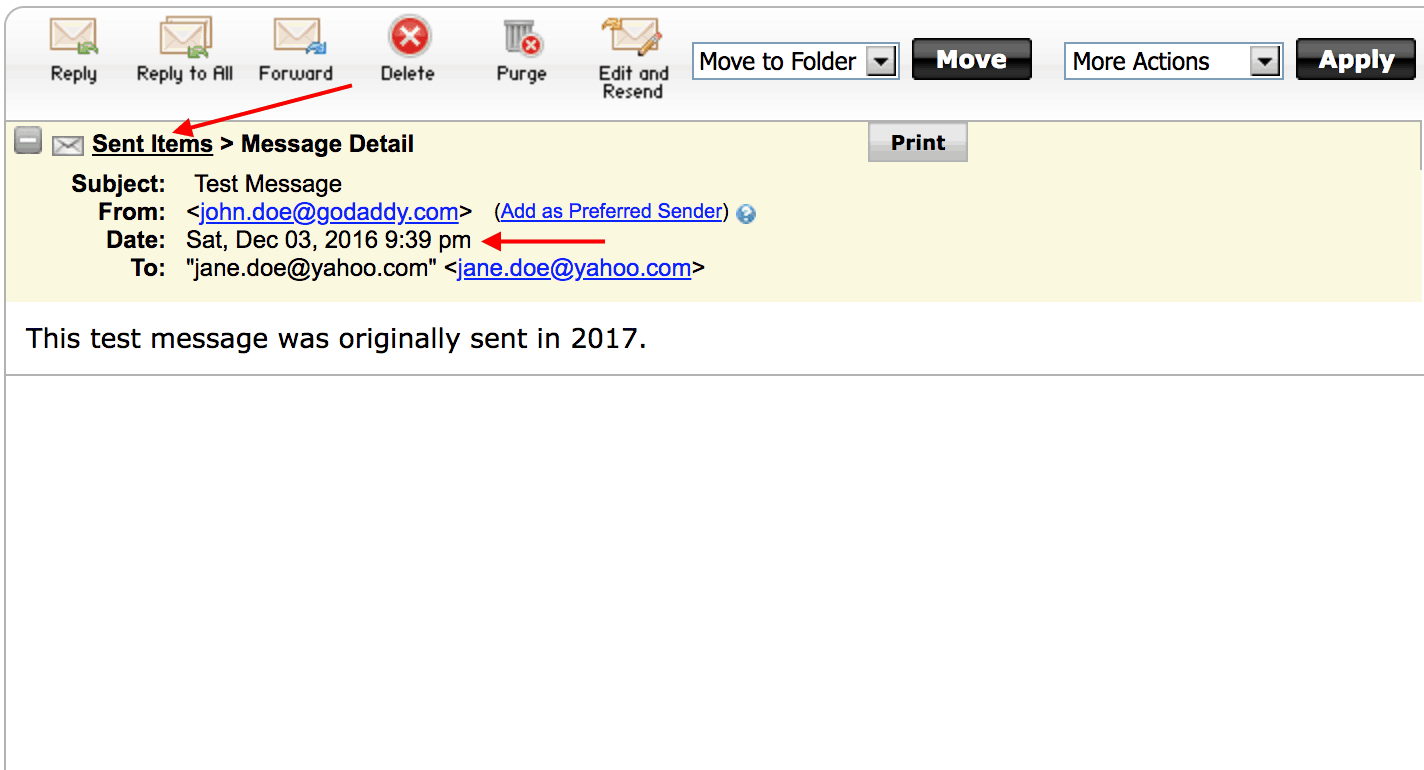
The message looks as follows on GoDaddy’s webmail interface:
As seen in the screenshot above, the message is listed under the “Sent Items” folder in the mailbox, and it has a date of Dec 3, 2016.
Proud of his accomplishment, the perpetrator invites the forensic examiner to review his mailbox and authenticate the message.
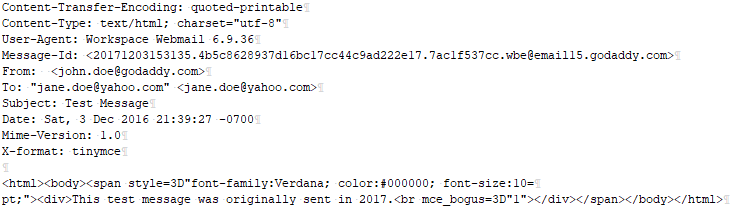
The forensic examiner acquires the message from GoDaddy over IMAP and finds that the raw message looks as follows:
The User-Agent: Workspace Webmail 6.9.36 header field is consistent with an email sent via GoDaddy webmail. Basic email metadata mirror what we see in GoDaddy’s webmail user interface. But the examiner caught a big break here: the Message-Id header field contains what seems to be a timestamp.
Message-Id: <20171203153135.4b5c8628937d16bc17cc44c9ad222e17.7ac1f537cc.wbe@email15.godaddy.com>
The Internet Message Format specification defines the Message-ID field as follows:
The “Message-ID:” field provides a unique message identifier that refers to a particular version of a particular message. The uniqueness of the message identifier is guaranteed by the host that generates it (see below). This message identifier is intended to be machine readable and not necessarily meaningful to humans. A message identifier pertains to exactly one version of a particular message; subsequent revisions to the message each receive new message identifiers.
How the Message-Id field is populated is implementation-dependent. The host can generate the identifier in its own way, as long as the uniqueness is guaranteed. In this case, it seems that GoDaddy prepended the timestamp 12/03/2017 15:31:35 to the Message-Id value. This is almost an entire year after the timestamp we see in the message, which warrants further review. The forensic examiner does her own independent research and testing to confirm whether or not emails sent via GoDaddy webmail have Message-Id values that start with the timestamp reflecting when the message was sent.
It is important to note that not all Message-Id values contain timestamps. Here is one from Yahoo!:
Message-ID: <2103767838.439800.1512250767353@mail.yahoo.com>
So, let’s think about what else the forensic examiner can find to support her finding.
Internal Date Message Attribute
Another data point we can check on an IMAP server to verify a message’s timestamp is the IMAP Internal Date Message Attribute. This date is not part of the message itself—it is kept by the server and indicates the date and time of the message on the server. Similar, in a way, to file system timestamps for files.
The IMAP 4 Specification indicates that when the APPEND command is used to add a message to a mailbox, the Internal Date Message Attribute should be set to the date/time argument supplied with the APPEND command, if present, or to the current date and time by default.
Luckily for the forensic examiner, when messages are added to a mailbox using most mainstream email clients, the APPEND command is issued without a date/time argument. So, in most cases, the Internal Date Message Attribute should reflect the date and time when the message was added to the mailbox.
In this case, when the examiner looks at the raw IMAP communication log that Forensic Email Collector provides, she sees the following line:
INFO Imap(2)[6] Response: * 1 FETCH (UID 8 RFC822.SIZE 576 FLAGS (\Seen) INTERNALDATE “21-Jun-2018 17:51:47 +0000” ENVELOPE (“Sat, 3 Dec 2016 21:39:27 -0700” “Test Message” ((NIL NIL “john.doe” “godaddy.com”)) ((NIL NIL “john.doe” “godaddy.com”)) ((NIL NIL “john.doe” “godaddy.com”)) ((“jane.doe@yahoo.com” NIL “jane.doe” “yahoo.com”)) NIL NIL NIL “<20171203153135.4b5c8628937d16bc17cc44c9ad222e17.7ac1f537cc.wbe@email15.godaddy.com>”))
So, although the Origination Date found in the message header is 12/3/2016 21:39:27 (-07:00), the Internal Date kept by the server is 6/21/2018 17:51:47 (UTC). Based on the examiner’s findings so far, it looks like this message was originally sent in 12/3/2017 and then added to the mailbox on 6/21/2018. Let’s see if the examiner can find any additional evidence to support her findings.
Unique Identifier (UID) Message Attribute
The IMAP Protocol Specification defines the UID Message Attribute as a unique identifier that must not refer to any other message in the mail folder. Furthermore, UID values are assigned in a strictly ascending manner. Each message added to the mailbox is assigned a higher UID than the previous messages.
So, if our message with the fraudulent date was added to the mailbox after the fact, it should have a larger UID value compared to other genuine messages from the same time period.
In this case, checking the acquisition log confirms that the suspect message has, in fact, the largest UID value and sequence number in the “Sent Items” folder.
Because of this, it was also acquired as the last item in the “Sent Items” folder by Forensic Email Collector as acquisition takes place in ascending UID order. This corroborates the examiner’s finding that the suspect message was added to the mailbox on 6/21/2018 at 17:51:47 (UTC), which is just hours before the forensic examination.
Next Steps
The forensic examiner has found some interesting evidence from the email message itself and from the IMAP server. Two new dates have been identified: 12/03/2017, when the email message appears to have been sent based on its Message-Id, and 6/21/2018, when the email message appears to have been added to the IMAP mailbox.
The forensic examiner will now want to review the workstation where the suspect email message was created and sent, and look at a number of artifacts such as Shellbags, internet history, and LNK files and attempt to correlate the activity on the workstation to the information found on the suspect message and the IMAP server. With some luck, she might be able to determine which software the suspect used to download the email message, modify it and append it to the IMAP server. She might even find some evidence of the suspect Googling how to commit email forgery!
Conclusion
Forensic examiners review a long list of data points when authenticating email messages. In addition to the information one can find within the email message itself, email servers often contain metadata about a message that is stored outside of the message. Internal Date and Unique Identifier (UID) message attributes are two such data points that can be utilized to help confirm findings during forensic email investigations.
Additionally, when looking at an entire IMAP mailbox, forensic examiners can utilize the Internal Date and Unique Identifier (UID) message attributes to quickly identify and hone in on suspicious messages that have a significant discrepancy between their header dates and internal dates and sequence numbers.