Forensic Email Collector™
Expertly preserve email evidence without breaking a sweat. Get plug & play output for digital forensic investigations and eDiscovery.

Expertly preserve email evidence without breaking a sweat. Get plug & play output for digital forensic investigations and eDiscovery.
We all run into cases where collecting a mailbox as a whole is not an option—often due to privacy or timeframe concerns. On the other hand, eDiscovery and digital forensics workflows often involve a full collection, followed by post-acquisition searches.
Forensic Email Collector solves this problem in a creative way. You can perform instant in-place searches on mailboxes on the server before the acquisition and forensically preserve only the search results. No need to create labels, tag documents, or make any changes to the target mailbox.
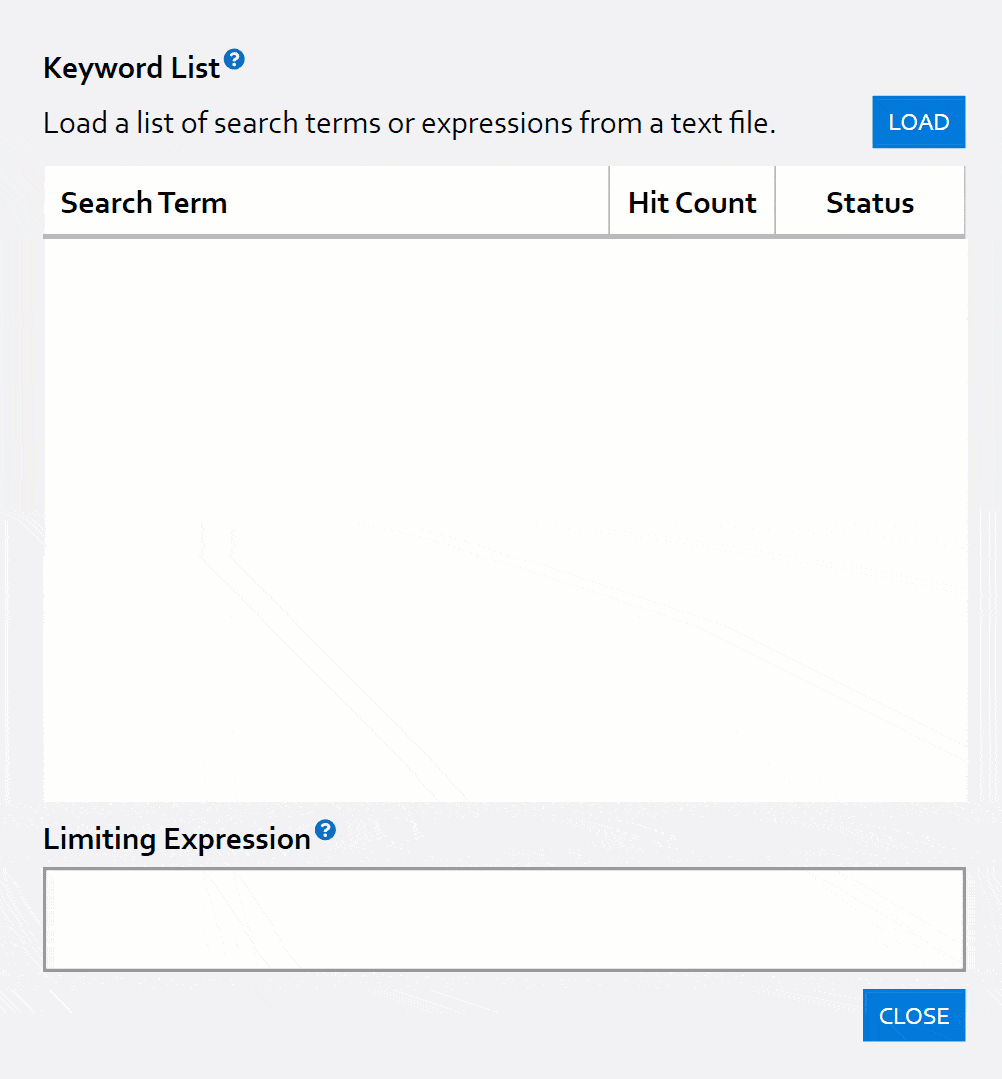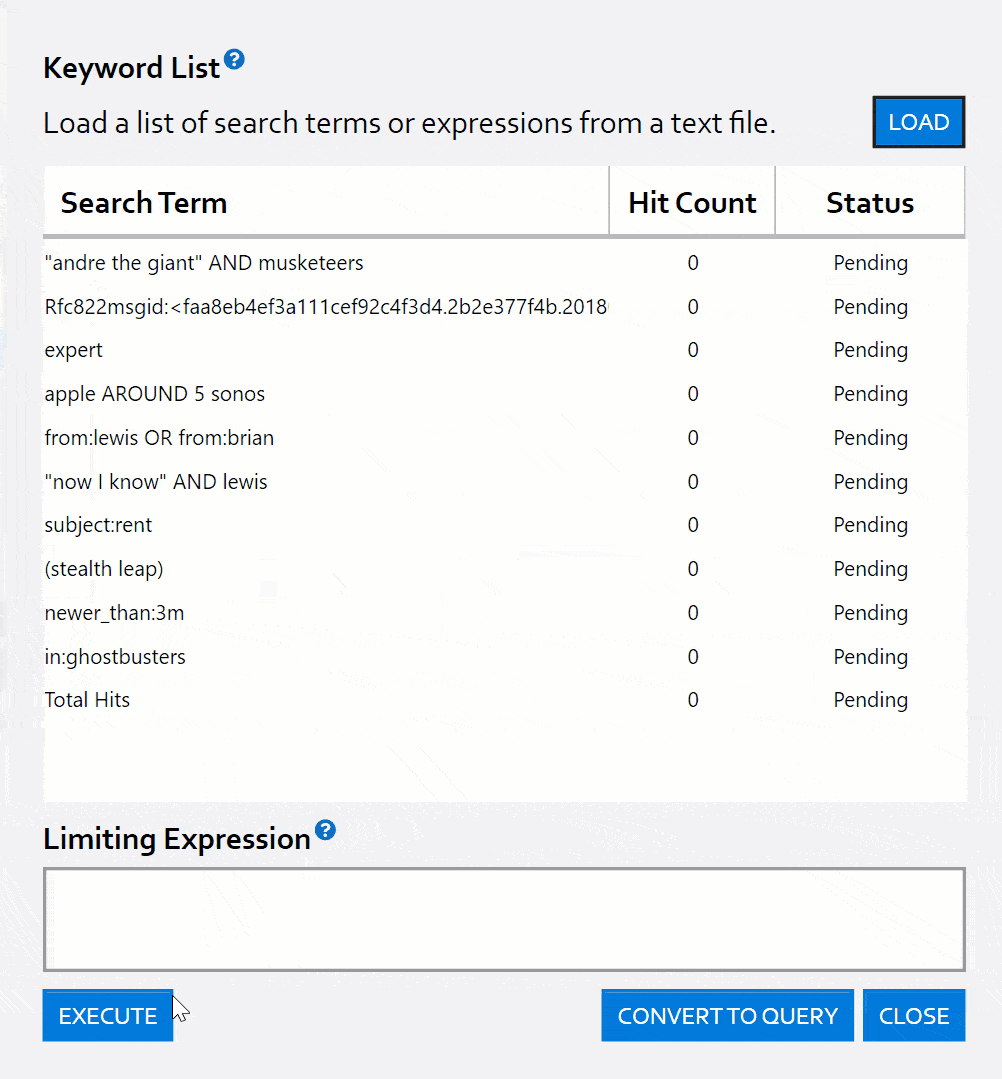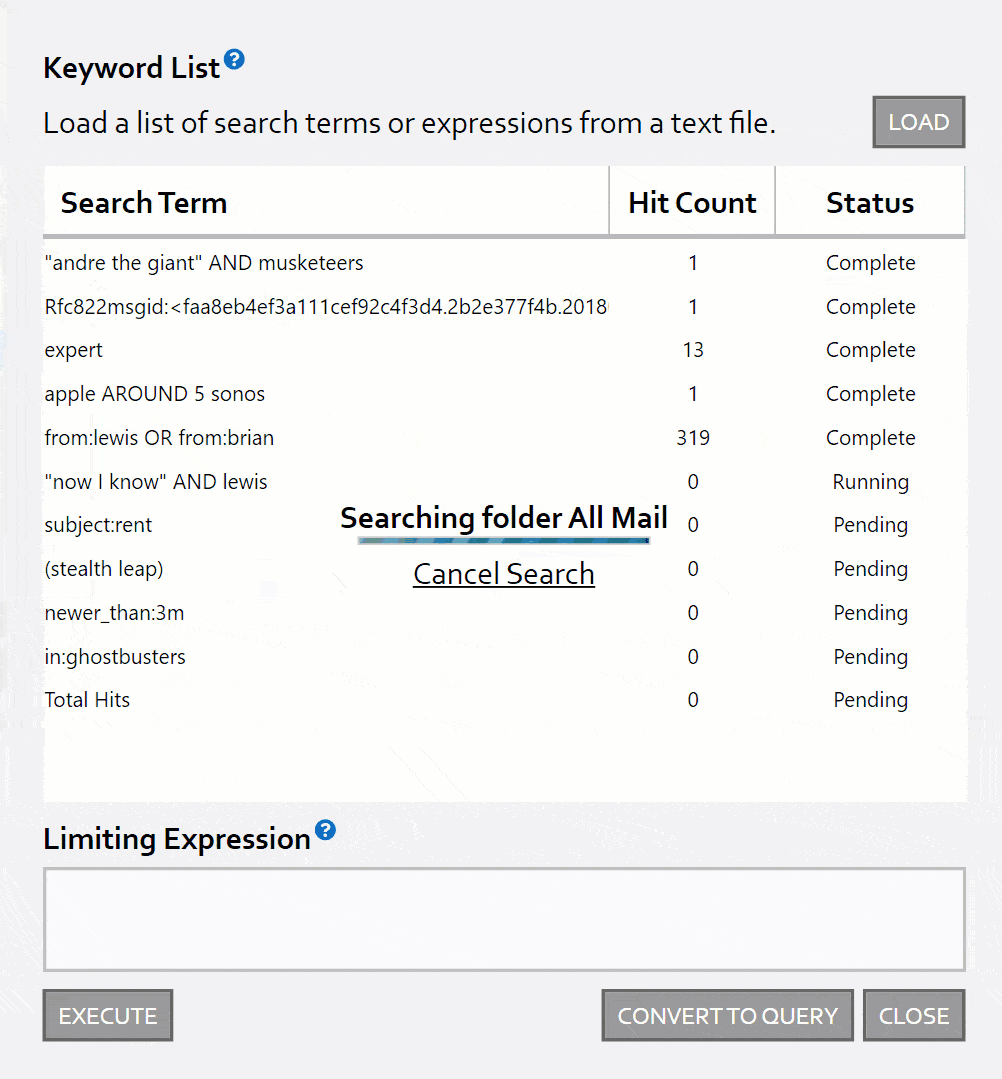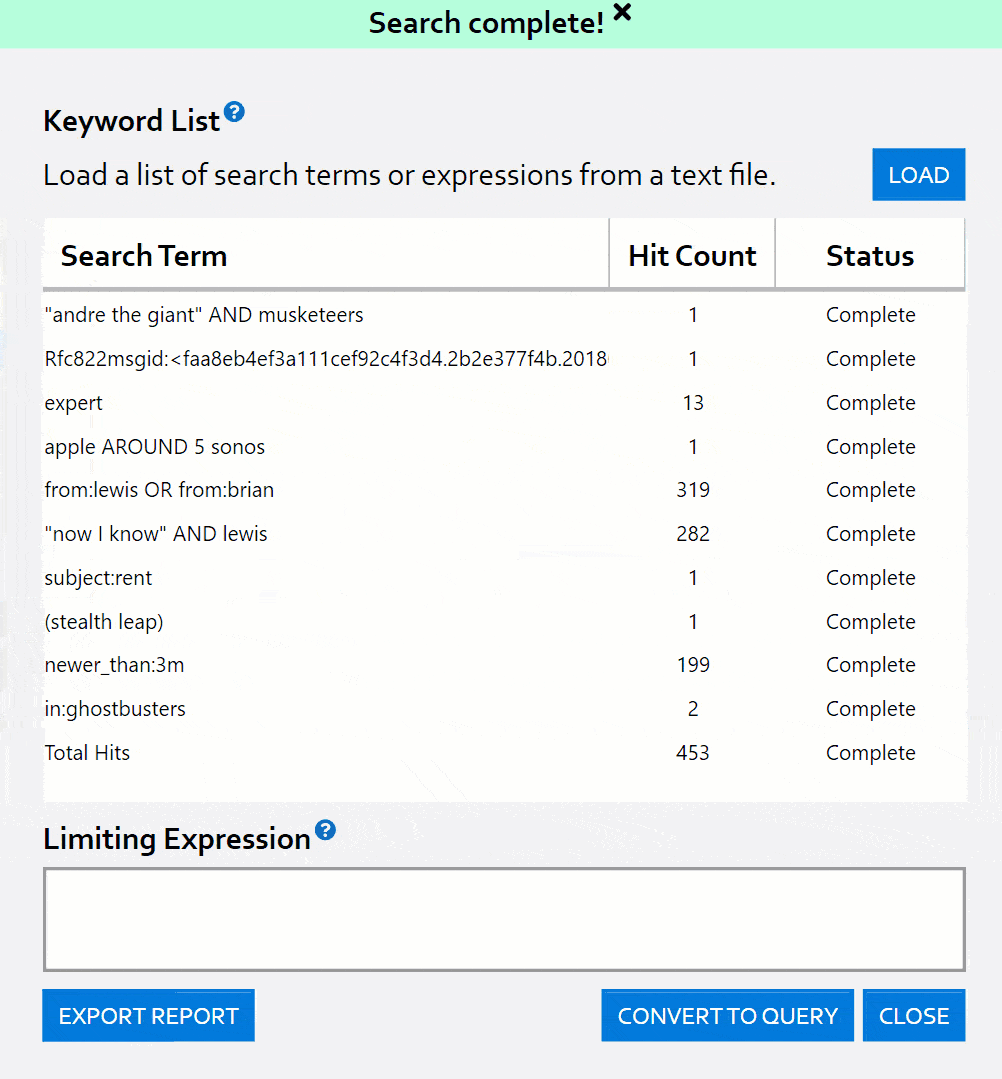
Have a list of terms or expressions to search for? You can load them from file and get a hit count report per line with a few clicks!

Files attached to emails as hyperlinks to a cloud storage system can throw a monkey wrench into your forensic preservation. The linked attachments often require authentication and are inaccessible unless handled as part of the initial acquisition.
Forensic Email Collector automatically detects and acquires Google Drive attachments and revisions of emails during Gmail and Google Workspace acquisitions! Preserved cloud items are presented in a neat package with their parent emails to maintain parent/child relationships.
“In 20 years - this has been the best email collection tool, bar none. If you are in a hot seat with a deadline - like I was - and need a tool for a large scale collection - have no fear, this is the tool. Equally important was the support that I received on the spot!”
Jason Conley, CECI, CCO, CCPAJason Conley & Associates
“Your tool rocks! Finally a tool that does what it says it does! Thank you!”
Josh FazioPartner @ InfoForense
“I love your product. Even though I have the ability to download PSTs directly from O365, I use FEC every time. Why? Because FEC works EVERY time and “O365 export to PST” fails more often than it works.”
Jason Park, CCCE, CCFPCyber Security & e-Discovery @ Fortune 500
Authenticating into the target mailbox is often the first hurdle when acquiring emails. Forensic Email Collector makes this a breeze with three powerful options.
FEC supports modern authentication via OAuth 2.0 when working with O365, Gmail / G Suite, and Microsoft’s consumer accounts such as Hotmail and Outlook.com. This allows both multi-factor authentication workflows and single sign-on (SSO) solutions such as Okta. No need to enable “access for less secure apps”.
Using FEC Remote Authenticator, custodians can authenticate FEC with their Gmail, G Suite, O365, and Microsoft consumer accounts from their own computer—Mac or PC. They can clearly see what data FEC has access to, and can revoke that access once the acquisition is complete. No need to share any passwords!
Who wants to learn everyone’s password or track end-users down to get authentication tokens when acquiring a large number of mailboxes from the same organization? FEC makes it possible to use a single set of administrator-level credentials to access end-user mailboxes when acquiring from G Suite, O365, or on-premises Exchange.

We have created Forensic Email Collector with the final act in mind—the courtroom. During each acquisition, FEC captures server metadata such as IMAP UIDs, Gmail message and thread IDs, internal dates, and numerous MAPI properties from Exchange servers. These values are then decoded and presented in an effective way to make your investigation a success.
If there was a hidden timestamp in that thread ID, wouldn’t you want to know about it before you wrote your expert report?
Some of the world’s most prestigious organizations—from law enforcement agencies to law firms, corporations, and service providers—trust Forensic Email Collector to secure email evidence in mission-critical projects.
Its accuracy, reliability, and outstanding performance make Forensic Email Collector the go-to tool of professionals for anything from single mailbox collections to enterprise-wide email preservation projects.













Forensic Email Collector doesn’t stop at emails. You can also forensically acquire events from Google Calendars and appointments, contacts, and notes from Exchange servers.
Just like emails, these items can be exported in MSG and PST formats in addition to generic formats such as iCalendar (.ics) and vCard (.vcf) depending on item type.
Forensic Email Collector can connect to most popular email servers and cloud email providers. You are not stuck with IMAP or POP for forensic email preservation.

FEC can connect to Exchange servers—including Office 365—via Exchange Web Services. You can preserve emails faster and more accurately, and without having to configure the target Exchange server for IMAP access.
FEC authenticates with Gmail and G Suite using OAuth and forensically acquires mailboxes at eye-watering speeds via Gmail API. Say goodbye to downloading the same message multiple times because of overlapping labels.

FEC uses Microsoft Graph API to connect to O365 mailboxes as well as Microsoft’s consumer accounts such as Hotmail, Outlook.com, and Live. Graph API provides support for modern authentication and powerful search capabilities.

FEC connects to IMAP & POP servers in a read-only manner and preserves email evidence without modifying the target mailbox. Outlook.com, Hotmail, Yahoo Mail, Zoho, iCloud and AOL Mail are just a few supported providers.
Exchange, Office 365, Graph, Exchange Web Services, EWS, Gmail, and G Suite are trademarks or registered trademarks of their respective holders. Use of them does not imply any affiliation with or endorsement by them.
We have added a few features to FEC to make sure it is a joy to use.
When preserving email evidence from an Exchange server, you may not immediately know the Exchange Web Services (EWS) endpoint URL. FEC utilizes the Exchange Autodiscover service to automatically configure itself using the target email address and password.
FEC includes built-in connection profiles—including host name, protocol, port and SSL settings—for hundreds of popular domain names used by email service providers such as Gmail, Yahoo, Outlook.com and iCloud. If the target email address matches one of the profiles, server settings are populated automatically for you.
As soon as you type the target email address, FEC checks the domain name to see if it fits one of the pre-configured profiles such as Gmail, Outlook.com, Yahoo, etc. If it does not, it looks up the mail exchanger records (MX records) to determine the mail servers handling email messaging for the target user’s domain.
When you use the IMAP protocol, FEC keeps a detailed log of IMAP communications with the server in addition to its standard acquisition and exception logs. You can do a play-by-play of what FEC asked the server and how the server responded if that’s your thing.
As soon as we process your order, we will email you an electronic download link and your license key.