What is Obliterator?
I have been tasked with mailbox sanitization numerous times, and I know it isn’t fun without the right tools. This is a common request, especially in connection with trade secret misappropriation cases. Usually, one of the conditions of the settlement involves searching devices for files containing the misappropriated trade secrets, and then logging and removing those items.
When it comes to mailbox remediation, Forensic Email Collector has been helpful in identifying and logging the items to be deleted from a mailbox. But, since it is a forensic tool, FEC is not capable of altering the source mailbox. So, it didn’t help with the removal part.
Last year, we received an inquiry from one of our users and decided to put together a free tool that does the following:
- Receive a tab-delimited list of messages to be deleted, including their cryptographic hashes and IDs
- Request each item on the list from the email server by its ID, hash it in memory, and compare the hash to the hash supplied on the list above UPDATE (May 5, 2021)—this applies to IMAP remediation only, not Gmail API or EWS
- If the hashes match, remove the item from the mailbox UPDATE (May 5, 2021)—this applies to IMAP remediation only, not Gmail API or EWS
- Keep detailed logs of the operation
Today, we are releasing this free tool to the public with the hope that it might be helpful to other forensic examiners.
UPDATE (May 5, 2021):
Obliterator now supports Gmail API in addition to IMAP. When remediating via Gmail API, you can target an individual Gmail or Google Workspace mailbox via OAuth, or multiple Google Workspace mailboxes using domain-wide delegation of authority.
UPDATE (October 7, 2021):
Obliterator now supports Exchange Web Services (EWS) in addition to Gmail API and IMAP. This allows the remediation of mailboxes on on-premises Exchange as well as O365.
Input List
Obliterator requires a tab-delimited list of items to be deleted.
A. IMAP
When using IMAP, the input list should contain the following fields (order doesn’t matter):
ID: This is a sequential integer number you can assign to the items (e.g., 1,2,3, etc.)
Service ID: This is the UID and UID Validity of the item as provided by the server concatenated and Base64 encoded. Obliterator will use this information to request the item. (e.g., “IAAA3p”)
Folder: This is the IMAP folder where the message is located (e.g., “Inbox”)
MIME Hash [Sha256]: This is the SHA-256 hash of the raw MIME message
Here is how the list file should look (columns should be separated by tabs):
| ID | Service ID | Folder | MIME Hash [Sha256] |
|---|---|---|---|
| 1 | IAAA3p | Sent | 06C8CA9A77754F35098AC8F64A19D545C2ED44732130B33777046A755054A852 |
| 2 | IAAA4P | Sent | 92D88DF6E11E3A926E17D9B413A51FD0C1D929521ED71054219C520AAAA050EE |
| 3 | IAAA4Z | Sent | 232C087F831A29331DA0E51D0A669C72F3FFDE06C2966CEFADABFC78E3E3292D |
| 4 | IAABFN | Sent | A32BD508723688DB203C0BDB5F7D5922954F53DE223CFC9F28ACBE95E2075673 |
You can download a copy of this file here: Sample Input List
B. Gmail API
When using Gmail API, the input list should contain the following fields (order doesn’t matter):
ID: This is a sequential integer number you can assign to the items (e.g., 1,2,3, etc.)
Service ID: This is the message ID Gmail assigns to messages. (e.g., “17937bf1b3dbb3bb”)
Here is how the list file should look (columns should be separated by tabs):
| ID | Service ID |
|---|---|
| 1 | 17937bf1b3dbb3bb |
| 2 | 178ea9a306924c29 |
| 3 | 178db20fc49d6bc8 |
| 4 | 178c67aae8cc70fa |
Important Note: The Service IDs are not interchangeable between IMAP and Gmail API. For instance, you cannot use IMAP UIDs when remediating emails via Gmail API.
C. Exchange Web Services (EWS)
When using Exchange Web Services (EWS), the input list should contain the following fields (order doesn’t matter):
ID: This is a sequential integer number you can assign to the items (e.g., 1,2,3, etc.)
Service ID: This is the message ID Exchange / O365 assigns to messages. (e.g., “AAMkADZiZjAyYzg1LTExNGEtNGQzYS04N2ZlLTE0WjkxYmY0YTdjOABGAAAAAACr3SEOXvYwRIElNTI+ZkKpBwC/dZ5AXYFrRZKzfGUxmn5mAAAAAAEMAAC/eZ5AXYFrRZKzfGUxmn5mAAMtOgn9AAA=”)
Here is how the list file should look (columns should be separated by tabs):
| ID | Service ID |
|---|---|
| 1 | AAMkADZiZjAyYzg1LTExNGEtNGQzYS04N2ZlLTE0WjkxYmY0YTdjOABGAAAAAACr3SEOXvYwRIElNTI+ZkKpBwC/dZ5AXYFrRZKzfGUxmn5mAAAAAAEMAAC/eZ5AXYFrRZKzfGUxmn5mAAMtOgn9AAA= |
| 2 | AAMkADZiZjAyYzg1LTExNGEtNGQzYS04N2ZlLTE0WjkxYmY0YTdjOABGAAAAAACr3SEOXvYwRIElNTI+ZkKpBwC/dZ5AXYFrRZKzfGUxmn5mAAAAAAEMAAC/eZ5AXYFrRZKzfGUxmn5mAAMtOgn7AAA= |
| 3 | AAMkADZiZjAyYzg1LTExNGEtNGQzYS04N2ZlLTE0WjkxYmY0YTdjOABGAAAAAACr3SEOXvYwRIElNTI+ZkKpBwC/dZ5AXYFrRZKzfGUxmn5mAAAAAAEMAAC/eZ5AXYFrRZKzfGUxmn5mAAMtOgn6AAA= |
| 4 | AAMkADZiZjAyYzg1LTExNGEtNGQzYS04N2ZlLTE0WjkxYmY0YTdjOABGAAAAAACr3SEOXvYwRIElNTI+ZkKpBwC/dZ5AXYFrRZKzfGUxmn5mAAAAAAEMAAC/eZ5AXYFrRZKzfGUxmn5mAAMtOgn3AAA= |
Important Note: The Service IDs are not interchangeable between IMAP and EWS. For instance, you cannot use IMAP UIDs when remediating emails via EWS.
How to Create The Input List
If you are a user of Forensic Email Collector, you probably noticed that the above format is the format of the Downloaded Items log file FEC produces using its default options. So, in order to create the input list in FEC:
- Start a new IMAP, Gmail API, or EWS acquisition depending on your target type.
- If using IMAP, keep the MIME output option checked (you can add other output formats if needed) and keep the default value for hashing algorithm (SHA-256).
- Perform an in-place search to identify the items to be deleted.
- Complete the acquisition.
Having completed the steps above, you will now have a preservation copy of the items to be deleted (great to keep a copy before you delete them) as well as the input list needed for Obliterator. You can now run Obliterator and point it to the Downloaded Items Log file FEC produced.
Alternatively, you can acquire the entire mailbox, identify the items to be deleted using other tools such as a forensic investigation tool or an eDiscovery review tool, and create a subset of the Downloaded Items Log for Obliterator based on the results of your review. If you choose this option, we recommend that you use item-level output in your initial acquisition (e.g., EML and/or MSG) and overlay the Service ID values from FEC’s Downloaded Items Log to your forensic or eDiscovery review tool. This would make it easy to export a subset list of Service IDs for remediation once your filtering and review are complete.
If you are not a Forensic Email Collector user, you can put together the input list manually or by using a script. When calculating the hash of each email message, it is important to hash the raw MIME message (RFC 5322) presented by the server without any manipulation.
Email Remediation Using Obliterator
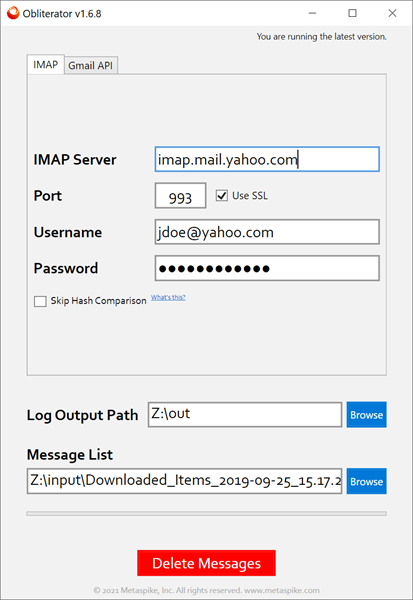
A. IMAP
Once you have the input list described above, you can provide Obliterator with the target server’s details, credentials for the target mailbox, the output path where the logs will be written, and the path to the input list. Here is a screenshot:
The Skip Hash Comparison option determines how Obliterator identifies the messages to be deleted. If checked, Obliterator uses a combination of IMAP UID, IMAP folder name, and UIDVALIDITY values. If unchecked, Obliterator also downloads each message, hashes it, and compares the hash to the hash provided in the input list.
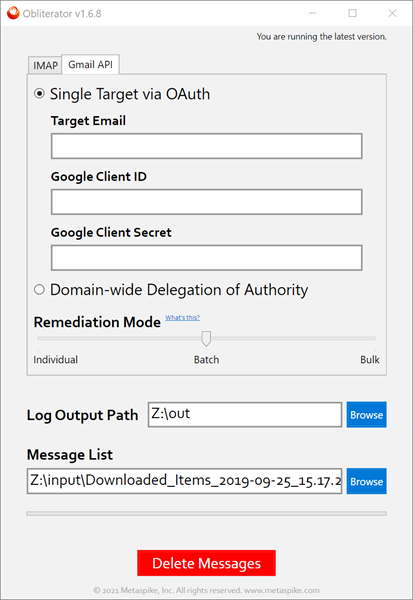
B. Gmail API
When using Gmail API, you have two main decisions to make:
1. Authentication Method: You can authenticate into an individual user’s mailbox using OAuth, or at the organization level using domain-wide delegation of authority. For OAuth, you will need to create your own Gmail API credentials and supply the Client ID and Client Secret to Obliterator. The credentials will be used to authenticate with the target mailbox. It is important that you add “Gmail API” to your Google API project.
When using domain-wide delegation, configure domain-wide delegation as described in our domain-wide delegation documentation for FEC with one difference—you need to add the ‘https://mail.google.com’ scope to the authorized scopes. If you are using the service account for Obliterator only, this is the only scope you need. You can then import the JSON file into Obliterator and use it for authentication.
Important Note: If you are using domain-wide delegation, you need to add a third column to your input list named TargetEmail. This column should be populated with the email address for each target. This way, you can compile a combined list of messages for multiple end-users, and tell Obliterator which message belongs to which mailbox.
2. Remediation Mode: Obliterator is able to operate in three different modes depending on your needs:
-
- Individual: In this mode, a delete request will be issued for each message one at a time.
- Batch (default): In Batch mode, Obliterator combines the delete requests into batches to improve performance.
- Bulk: In this mode, a bulk request will be submitted to Google for deletion. This is significantly faster but does not guarantee whether the messages were found in the target mailbox or if they even existed at all.
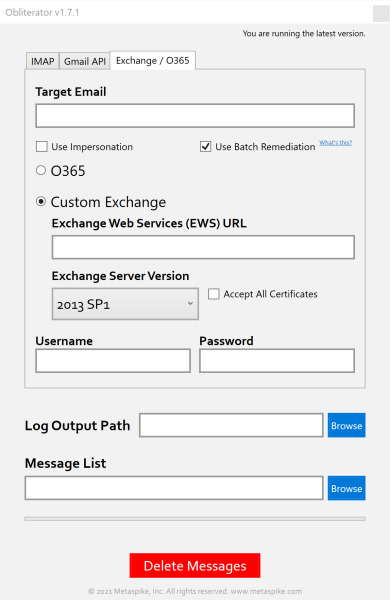
3. Exchange Web Services (EWS)
Obliterator supports both legacy authentication (i.e., username / password) and modern authentication (i.e., OAuth) when connecting to an Exchange server via Exchange Web Services. If you would like to use modern authentication, you will need to register your own Microsoft Azure App and supply Obliterator with its Client ID. You can accomplish this as follows:
- Visit https://portal.azure.com
- Go to App Registrations (https://portal.azure.com/#blade/Microsoft_AAD_IAM/ActiveDirectoryMenuBlade/RegisteredApps)
- Click + New registration
- Provide a name for your App
- Choose the “Accounts in any organizational directory” option
- For the redirect URL, choose Public client/native and enter http://localhost
- Click Register
- Go to API permissions
- Add Microsoft Graph > EWS.AccessAsUser.All (Delegated) as an API permission
- Once registration is complete, you can go to the “Overview” page for your App and copy its “Application (client) ID”. This is the value Obliterator needs.
Impersonation
The “Use Impersonation” setting controls whether you will be authenticating with the Exchange server as the end-user, or using central credentials (e.g., via a service account). You can configure impersonation as described here.
Remediation Mode
If you choose the “Use Batch Remediation” option, Obliterator would send the deletion requests to the server in batches to improve performance.
Accept All Certificates
This option controls whether Obliterator should accept all SSL certificates when connecting to the target server. Can be helpful when connecting to an on-premises Exchange server with an expired or invalid SSL certificate. Ordinarily, you should leave this option unchecked.
Important Note: When remediating Exchange / O365 mailboxes, an important concern is the retention capabilities built into the server. If not addressed, items that you delete can be retained by the server depending on its configuration. We recommend reading the following relevant articles from Microsoft:
Delete items in the Recoverable Items folder of cloud-based mailboxes on hold
Clean up or delete items from the Recoverable Items folder in Exchange Online
Get Your Copy
System Requirements
- Windows 7 SP-1 or later
- .Net Framework 4.6.1 (download from Microsoft)
- If running on Windows 7, make sure that the KB4457144 Windows update has been installed
Changelog
You can find Obliterator’s changelog in the Changelog tab on the right edge of this page.